A newly discovered phishing campaign, tracked as UNK_CraftyCamel, has been targeting aviation and satellite communications organizations in the UAE using a sophisticated Golang-based backdoor dubbed Sosano. The attackers exploited a compromised email account of INDIC Electronics, an Indian electronics company, to send phishing emails that appeared legitimate to the victims. These emails contained malicious polyglot files and disguised shortcuts, ultimately leading to the execution of the Sosano malware, which grants attackers remote access to the infected systems. The attack demonstrates advanced obfuscation techniques and the use of trusted third-party compromise, highlighting the growing sophistication of state-aligned cyber espionage operations.
Understanding the Key Components of the Attack
What is a Golang Backdoor?
A Golang backdoor is a malicious software implant written in the Go programming language (Golang), designed to provide attackers with unauthorized access to a compromised system. Go-based malware is increasingly favored by threat actors due to its cross-platform compatibility, ease of obfuscation, and resistance to reverse engineering. Such backdoors allow attackers to execute commands, exfiltrate data, or deploy additional payloads stealthily.
What is Sosano?
Sosano is a newly discovered Golang-based backdoor used in this attack campaign. It has a limited but effective set of functionalities, such as:
- sosano – Retrieve or change the current directory.
- yangom – Enumerate files and directories.
- monday – Download and execute additional payloads.
- raian – Delete or remove directories.
- lunna – Execute shell commands.
Its primary purpose is to establish a connection with a Command-and-Control (C2) server, enabling attackers to issue further commands for espionage or data theft.
Who is UNK_CraftyCamel?
UNK_CraftyCamel is the threat actor cluster behind this attack campaign. Proofpoint researchers identified this group but have not yet linked it to any known Advanced Persistent Threat (APT) groups. However, there are indications that it may be Iran-aligned, potentially affiliated with the Islamic Revolutionary Guard Corps (IRGC). The group specializes in highly targeted phishing campaigns that focus on aviation, satellite communications, and other critical industries.
What is INDIC Electronics?
INDIC Electronics is an Indian electronics company that was compromised in this attack. The attackers gained access to its email account, using it as a trusted source to send phishing emails to the actual targets in the United Arab Emirates (U.A.E.). Since INDIC Electronics had an existing business relationship with the victim organizations, emails from its domain appeared legitimate and bypassed initial suspicion.
How did the Attack take place?
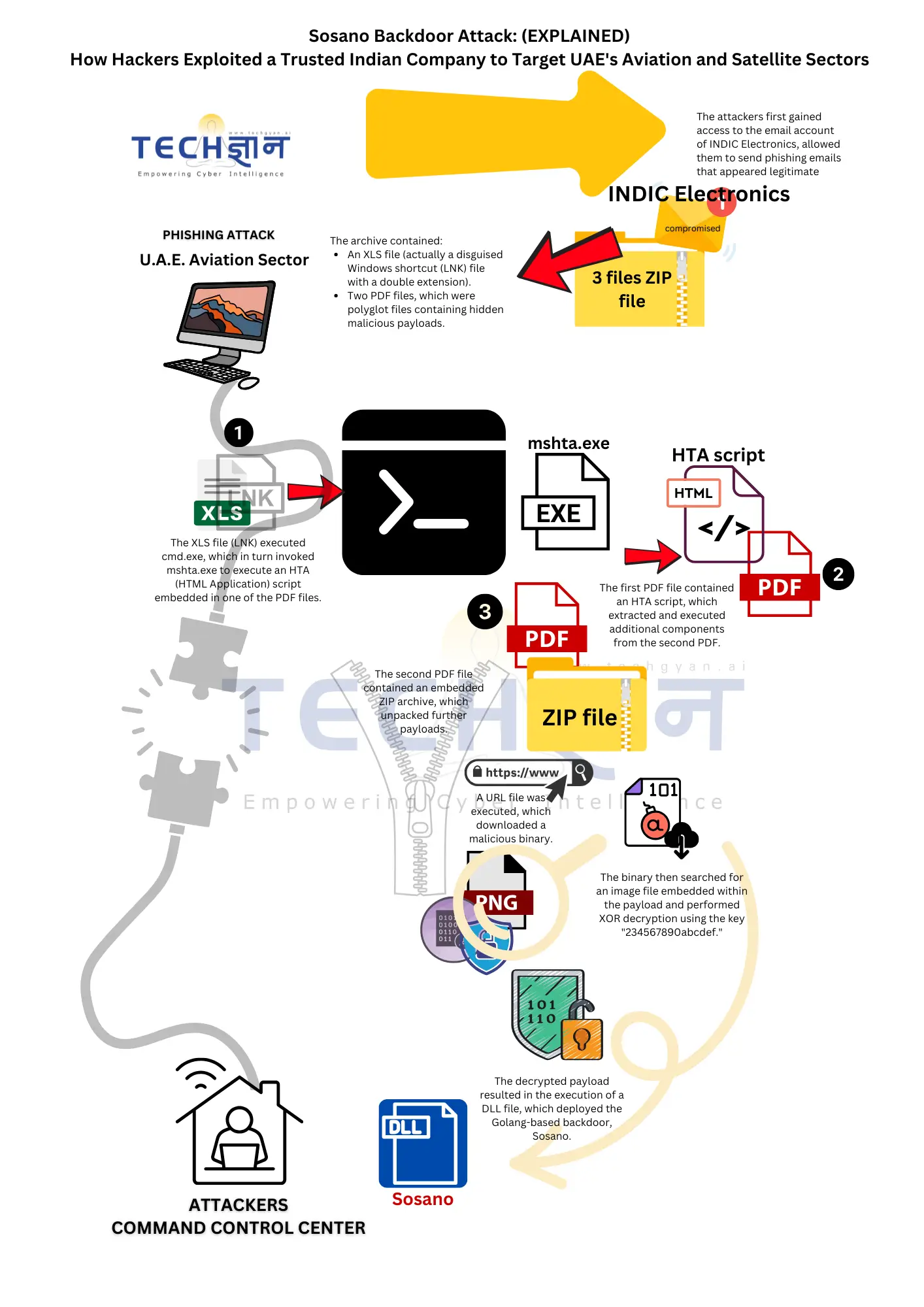
- UNK_CraftyCamel compromised INDIC Electronics’ email system to distribute phishing emails.
- These emails contained links to a malicious domain impersonating INDIC Electronics (indicelectronics[.]net), which hosted a ZIP archive containing multiple malicious files.
- The ZIP archive led to the execution of the Sosano Golang backdoor, allowing attackers to infiltrate the targeted systems.
- The attack focused on high-value targets in aviation and satellite communications sectors in the U.A.E., likely for espionage purposes.
The Sosano backdoor campaign highlights the increasing sophistication of state-aligned cyber espionage operations. By leveraging trusted third-party relationships and advanced obfuscation techniques, attackers managed to infiltrate critical sectors while evading traditional detection mechanisms.
Organizations must enhance their email security, endpoint defenses, network monitoring, and incident response capabilities to counteract such evolving threats effectively.
Cyber Threats Are Evolving – Is Your Organization Ready?
At Tech Gyan, we help businesses like yours stay ahead of cybercriminals by:
- Creating Cyber Awareness among employees to prevent attacks
- Building Strong Defenses to safeguard your business from threat
- Equipping Your Team with the knowledge to detect and respond to cyber risks
Don’t wait for a cyber-attack to happen! Secure your organization today.
Call +91 91529 66550 to book a FREE Cybersecurity Awareness Session for your employees!
Visit techgyan.ai to learn more.
Disclaimer:
The information provided in this document is for educational and informational purposes only. Techgyan does not guarantee the accuracy, completeness, or reliability of the information and is not responsible for any financial loss, legal implications, or damages resulting from the use of this content. Readers are advised to conduct their own research and consult cybersecurity professionals or legal experts before making any decisions based on the information provided. Techgyan does not endorse or promote any illegal activities and disclaims any liability related to the misuse of this information.


